What is Risk?
A risk describes a potential event that may cause harm to an organization, involving the possibility of causing adverse outcomes such as financial loss, reputational damage, or operational disruptions. Risks are often described by determining their likelihood of occurrence and the severity of their consequences (impact).
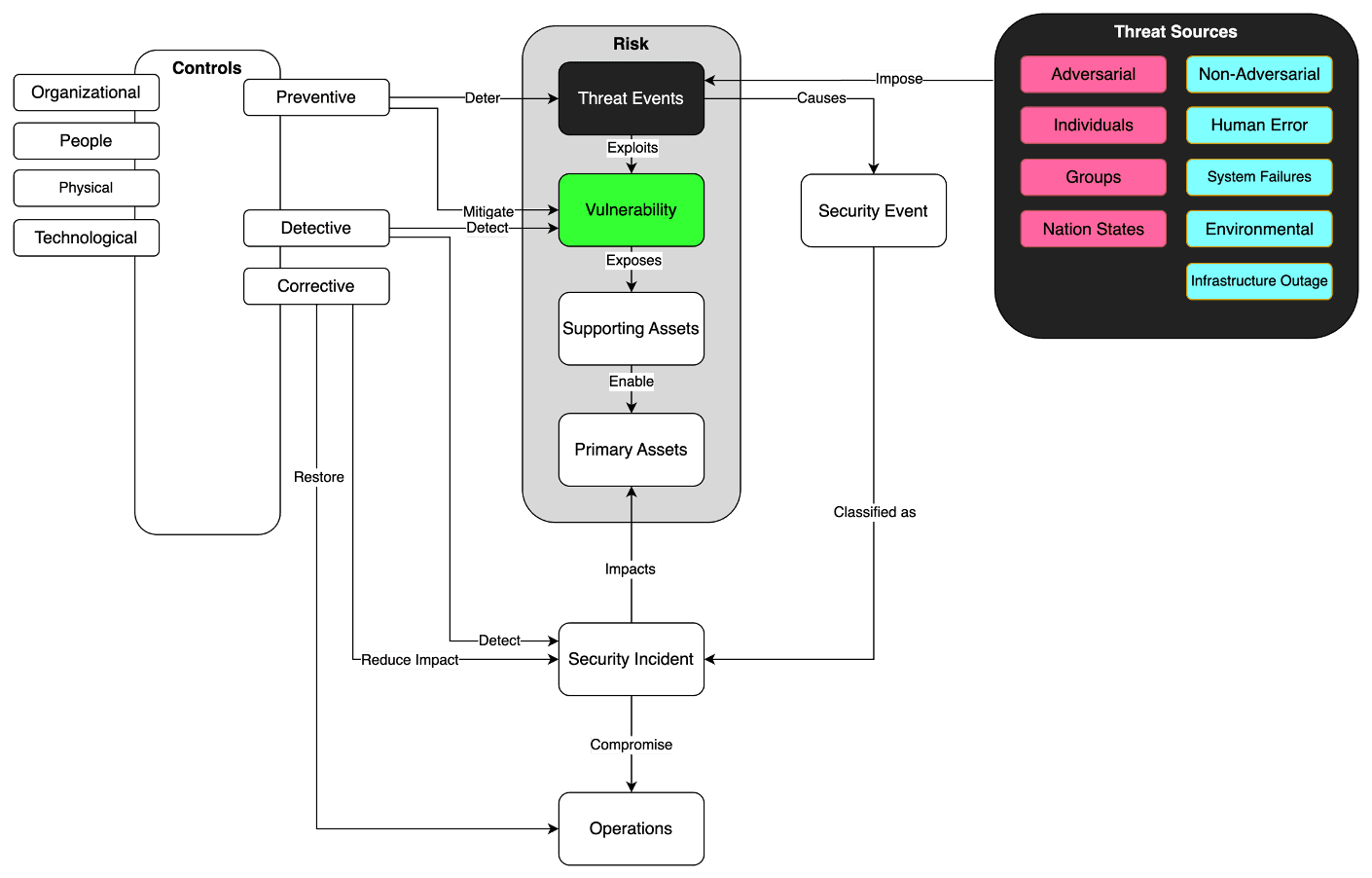
What is Risk Management?
Risk management is the process of identifying, assessing, and addressing risks that have the potential to negatively impact an organization’s ability to achieve its objectives. Effective risk management requires a thorough understanding of the threats that could harm an organization, the vulnerabilities that could be exploited, and the critical assets that need protection—all of which will be explored in the following sections.
Threat Sources
According to the National Institute of Standards and Technology (NIST), Threat Sources are defined as the origin of adverse events that could potentially harm an organization's assets and operations. These sources can be intentional or unintentional and can come from a variety of places such as nature, individuals, or organizations.
NIST categorizes Threat Sources into two main types:
Adversarial: These are intentional actions taken by individuals, groups, or organizations with the motive of causing harm or exploiting vulnerabilities. Adversarial threats include hackers, terrorists, insider threats, and even competitors.
Non-Adversarial: These are unintentional actions or natural events that could potentially harm an organization but lack a targeted intent. Examples include natural disasters like floods or earthquakes, accidental data deletion by an employee, or system failures due to a bug.
By understanding the nature and types of Threat Sources as defined by NIST, organizations can better prepare for, and mitigate, various risks that may affect them.
Threat Events
Threat sources impose threat events, which are specific actions or incidents that can potentially harm your organization. For example, a hacker (threat source) might attempt to break into your network (threat event).
Vulnerabilities
Vulnerabilities or so called predisposing conditions are the weak spots in systems and organisations where threat events can cause harm. These could be outdated software, weak passwords, or even a staff member who's not trained in security protocols.
Supporting Assets
Vulnerabilities often expose supporting assets, which are the various components of your system that aren't core to your business but are still important.
These can include:
Hardware: Servers, computers
Software: Applications, databases
Network: Internet connection, firewalls
Personnel: Employees, contractors
Sites: Physical locations like offices or data centers
Primary Assets
Primary assets are the essential elements an organization needs to operate effectively, such as core business processes or critical information. Supporting assets, on the other hand, enable these primary assets to function. For example, a web server hosting an online store (supporting asset) facilitates the sales process (primary asset) and is therefore vital for maintaining the organization’s business operations.
What do people in risk management do?
People working in risk management try to protect an organizations assets from threat sources. The knowledge needed to do so effectively varies deeply depending on the specific organization a risk manager works for. For example, a risk manager who works for an insurance company would have to know the regulatory requirements different regions impose, such as Solvency II in Europe, which states how insurance companies have to report on their risks and which government agencies they have to inform about their risk assessments.
To acquire such knowledge, risk managers have several options. Online courses offered by specialists are an established way increase one’s knowledge. Another way to do so is by acquiring risk management certifications , which are offered by companies like Treccert. These provide a very in depth knowledge on specific topics, but also come at a bigger cost, both time wise and money wise. A way to save a little on these high-tier certifications can be to use an exam voucher .




