Implementing an Information Security Management System (ISMS) in accordance with ISO 27001 can seem overwhelming at first. However, by following a structured approach, organizations of any size or industry can successfully manage the process. This guide outlines a 12-step approach to implementing ISO 27001, providing a roadmap to achieve compliance and enhance information security.

Step 1: Obtain Top Management Support
The foundation of a successful ISMS implementation begins with obtaining the support of top management. This step is critical because implementing an ISMS requires significant resources, such as time, money, and personnel. Top management must also play active roles within the ISMS, including setting the organization’s security objectives and endorsing the information security policy. Without their approval and ongoing support, the ISMS initiative is unlikely to succeed.
Step 2: Define the Scope of the ISMS
After securing management support, the next step is to define the scope of the ISMS. This involves deciding which parts, processes, or services of the organization will be covered by the ISMS. The scope should be aligned with the organization’s strategic objectives and risk environment. Clearly defining the scope ensures that all relevant information assets are protected and helps focus resources on the most critical areas.

Step 3: Conduct a Gap Analysis
Conducting a gap analysis is essential for understanding the current state of information security within the organization. This involves comparing existing information security practices against the requirements of ISO 27001. The gap analysis identifies areas where the organization already meets the standard and highlights deficiencies that need to be addressed. This step provides a baseline for developing an implementation plan.
Step 4: Develop an Information Security Policy
A high-level information security policy is a crucial component of an ISMS. This policy outlines the organization’s commitment to information security, sets objectives, and defines the overall approach to managing information security risks. It should be aligned with the organization’s strategic goals and provide direction for all subsequent information security activities. The policy should be communicated to all employees to ensure they understand their roles and responsibilities.

Step 5: Establish Information Security Awareness and Training Programs
Information security is everyone’s responsibility. To build a security-conscious culture, it is vital to establish processes for information security awareness and competence assurance. This includes conducting regular training sessions, workshops, and awareness campaigns to educate employees about the importance of information security, potential threats, and best practices. Ensuring that all staff members are aware of their responsibilities helps to reduce the risk of human errors and insider threats.

Step 6: Identify and Classify Information Assets
Identifying and classifying information assets within the scope of the ISMS is a critical step. This includes creating an asset inventory that lists all valuable information, hardware, software, and other resources. Once identified, assets should be classified based on their sensitivity and importance to the organization. Understanding what needs to be protected is essential for implementing effective security controls.

Step 7: Define Risk Management Methodology
With the asset inventory in place, the next step is to define methodologies for information security risk assessments and risk treatment. This involves establishing a process to identify, analyze, and evaluate risks associated with information assets. Organizations must also define their risk appetite and criteria for risk acceptance. A systematic approach to risk assessment and treatment ensures that the most significant risks are identified and addressed.
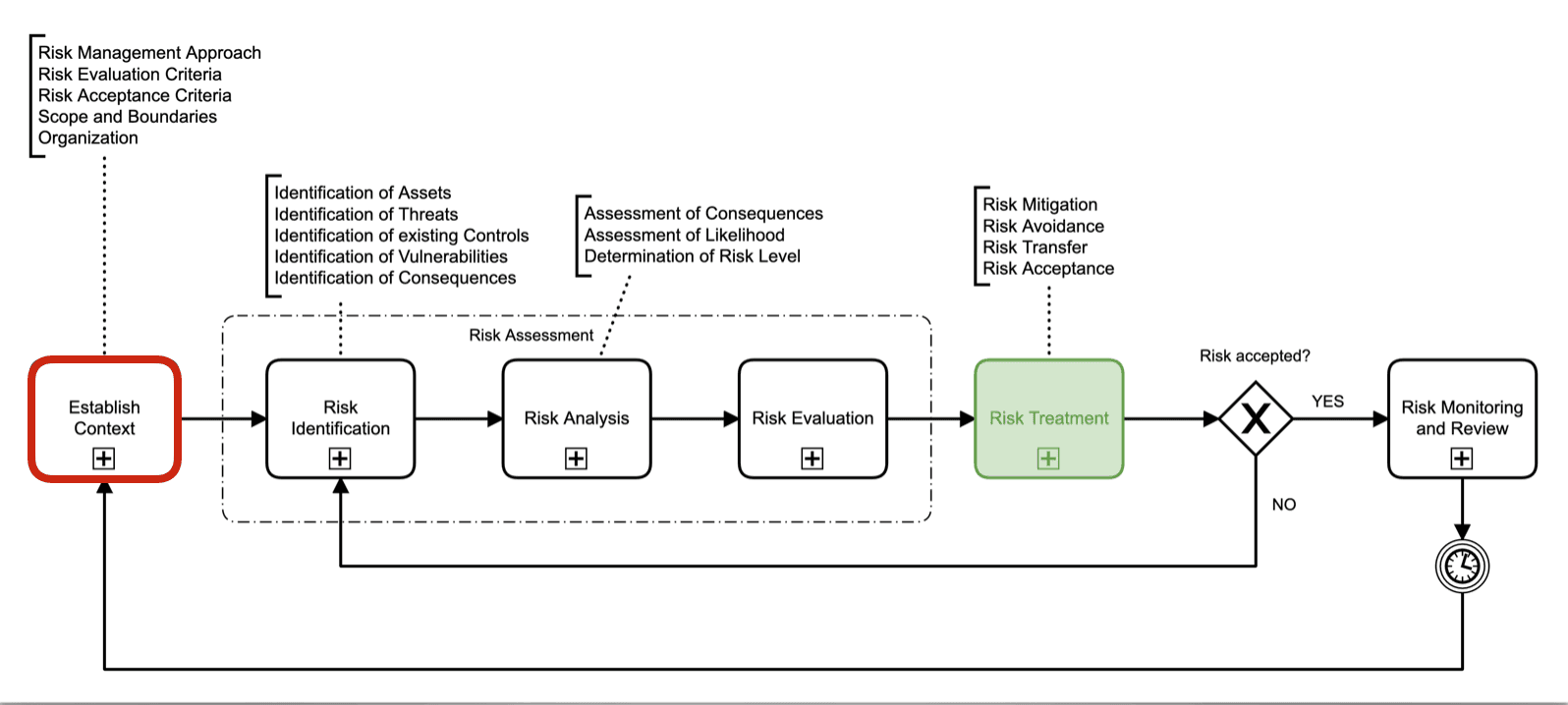
Step 8: Conduct Risk Assessments and Maintain a Risk Register
Following the established risk assessment process, organizations should conduct formal risk assessments to identify potential threats and vulnerabilities. The results of these assessments should be documented in a risk register, which tracks identified risks, their potential impact, and the likelihood of occurrence. The risk register serves as a living document that is regularly updated to reflect new risks and changes in the environment.

Step 9: Develop and Implement a Risk Treatment Plan
Based on the findings of the risk assessment, a risk treatment plan must be developed and implemented. This plan outlines the actions and controls required to mitigate identified risks to an acceptable level. Implementing the risk treatment plan may involve adopting new security technologies, updating policies and procedures, and enhancing employee training programs. This step is often the most time-consuming part of the implementation process, as it requires significant coordination and effort across the organization.

Step 10: Monitor and Evaluate ISMS Performance
To ensure the ISMS is effective, organizations must regularly monitor and evaluate its performance. This includes tracking key performance indicators (KPIs), conducting internal audits, and gathering feedback from employees and stakeholders. Performance evaluation provides valuable insights into the strengths and weaknesses of the ISMS, enabling organizations to make informed decisions about improvements.
Step 11: Implement Corrections and Continuous Improvement
The results of performance evaluations and audits should be used to implement corrections and improvements to the ISMS. This involves addressing any nonconformities, taking corrective actions, and making adjustments to policies, procedures, and controls. Continuous improvement is a core principle of ISO 27001, ensuring that the ISMS remains effective in the face of evolving threats and organizational changes.

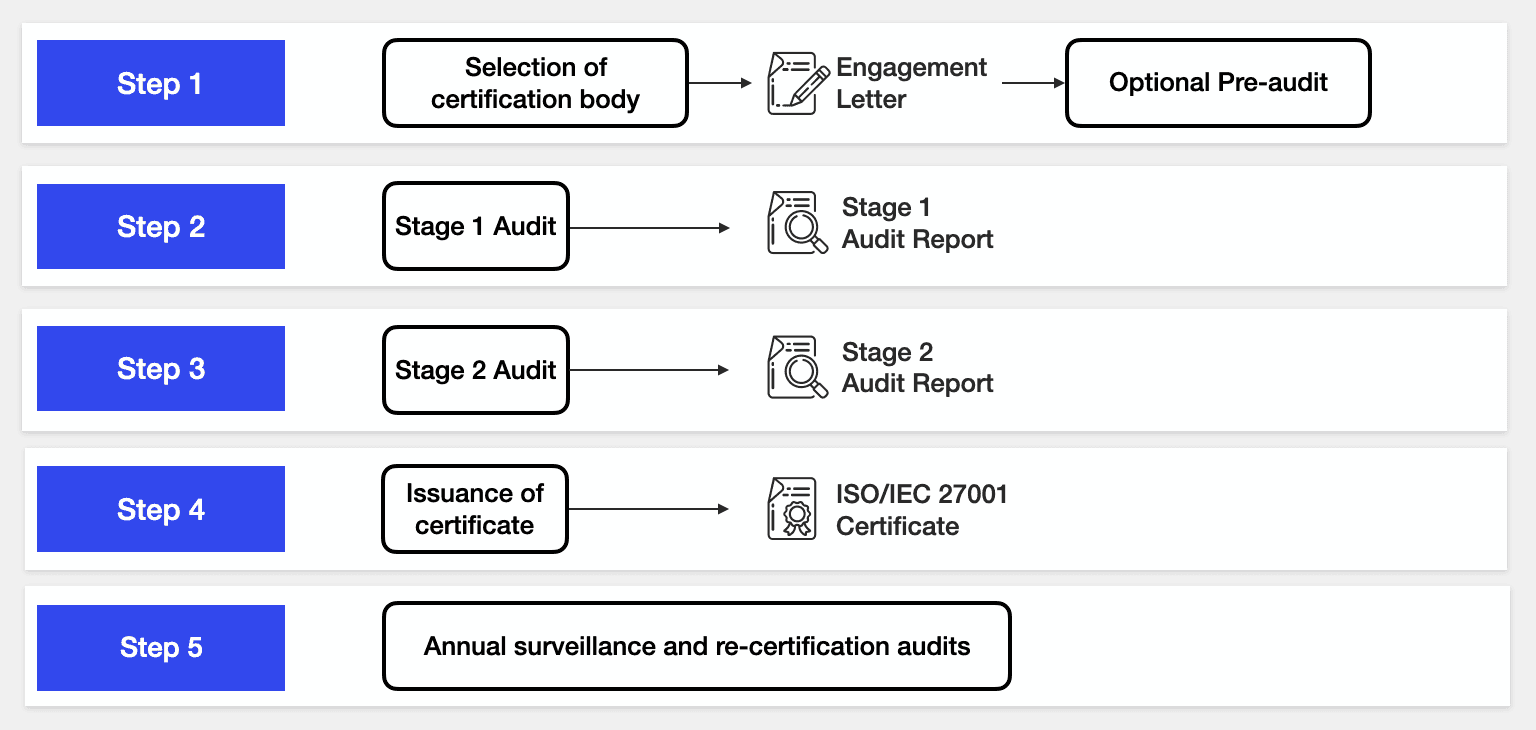
Step 12: Certification Audit
With the ISMS fully implemented and continuously improved, the organization is ready to seek certification. This involves engaging with a certification body to conduct an external audit of the ISMS. The certification process typically includes a Stage 1 audit (documentation review) and a Stage 2 audit (implementation review). Upon successful completion, the organization will be awarded ISO 27001 certification, demonstrating its commitment to information security.
Learn more about the certification process.
Conclusion
Implementing ISO 27001 requires a structured approach to managing information security. By following this 12-step process, organizations can systematically build a robust ISMS that protects sensitive information, mitigates risks, and ensures compliance with international standards. Even if an organization chooses not to seek certification, these steps provide a valuable framework for enhancing information security practices. For those new to ISO 27001, following the steps in order ensures a successful implementation, building a solid foundation for ongoing information security management.


