What is Annex A of ISO 27001?
Annex A of ISO/IEC 27001 is arguably the most renowned annex among all ISO standards. It provides a reference set of information security controls, which can be used for the treatment of identified information security risks. This article explores the structure of Annex A, the categorization of its controls, and its relationship with ISO/IEC 27002.
Structure of Annex A
Annex A is organized into four main sections, each corresponding to a specific theme of controls:
Organizational Controls: These controls focus on the policies, procedures, and frameworks within an organization. They include measures such as risk management frameworks, information security policies, and third-party management. There are 37 organizational controls listed in Annex A.
People Controls: These controls are related to the security practices of individuals within the organization. They address aspects such as employee awareness, training, and responsibilities. Annex A includes 8 people controls aimed at safeguarding against risks posed by human error or malicious insiders.
Physical Controls: Physical controls focus on securing the physical environment, including access to buildings, server rooms, and other facilities. Examples include surveillance systems, physical barriers, and access control mechanisms. Annex A outlines 14 physical controls.
Technological Controls: These controls pertain to the technology and systems used within an organization. They cover aspects such as network security, encryption, antivirus solutions, and system monitoring. Annex A details 34 technological controls.
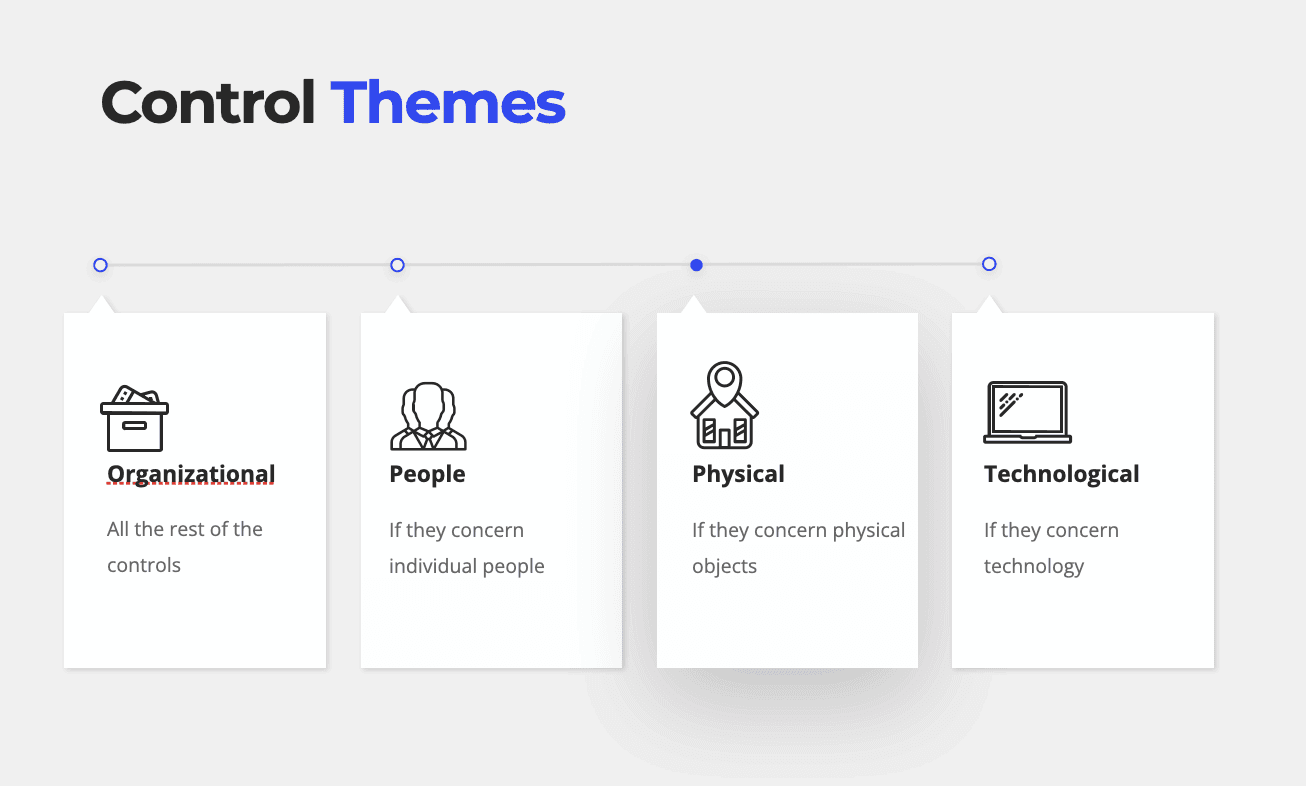
Each control in Annex A is assigned a unique identifier and categorized into one of these four control themes, making it easier for organizations to locate and apply the appropriate security measures.

The Role of ISO 27002 in Implementing Annex A Controls
Annex A only provides a high-level overview of each control, which includes only the control title and a brief control statement. For organizations or individuals new to information security management, this information might be too limited to fully understand or implement the controls effectively. This is where ISO/IEC 27002 comes into play.
ISO/IEC 27002 complements ISO 27001 by offering detailed guidance on how to implement the controls listed in Annex A. This comprehensive standard provides in-depth information for each control, structured into six components:
Control Title: A concise name for the control.
Attribute Table: Values associated with control attributes such as type and property.
Control Statement: A summary explaining what the control is and what it aims to achieve.
Purpose: Reasons for implementing the control and the benefits it offers.
Guidance: Recommendations and best practices for effective implementation.
Other Information: Additional context and references to related documents.
These sections provide clarity and actionable steps for implementing each control, making ISO/IEC 27002 a great companion to ISO/IEC 27001.
Categorization and Attributes of Controls
To help organizations effectively categorize and manage their information security controls, each control in ISO 27001 is associated with five key attributes:
Control Type: Defines whether the control is preventive, detective, or corrective.
Information Security Properties: Identifies whether the control helps preserve confidentiality, integrity, or availability of information.
Cybersecurity Concepts: Based on the ISO/IEC TS 27110 cybersecurity framework.
Operational Capabilities: Reflects the practitioner’s perspective of information security capabilities.
Security Domains: Groups controls into four domains: governance and ecosystem, protection, defense, and resilience.
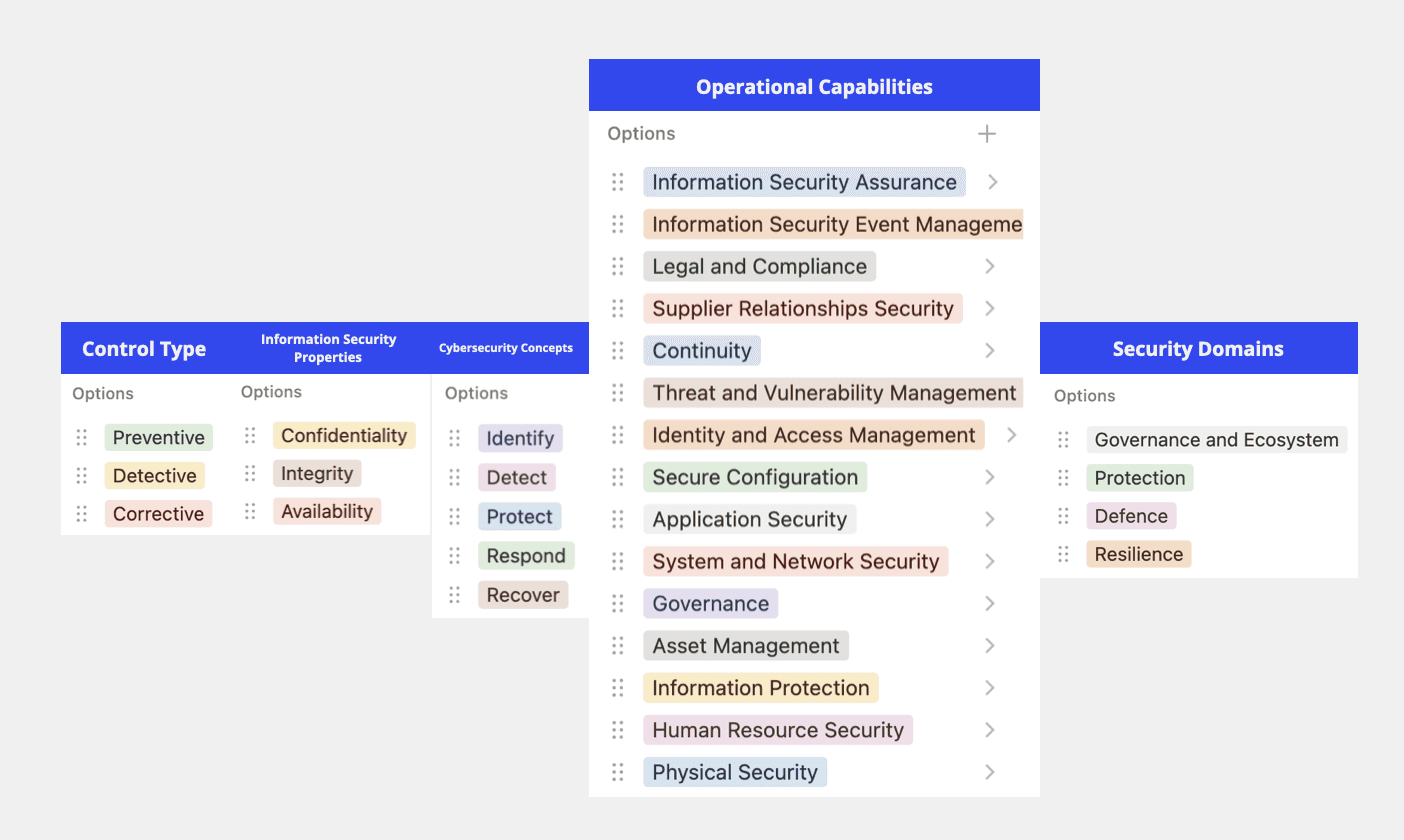
These attributes allow organizations to filter, sort, and present controls in a way that is meaningful to their specific needs, ensuring a tailored approach to information security.
Is Annex A Mandatory?
There is a common misconception that Annex A is mandatory for organizations trying to become ISO/IEC 27001 certified. However, this is not the case. ISO 27001 allows organizations the flexibility to choose any controls that best address their specific risks and security requirements. For example, organizations could theoretically select and implement controls from other frameworks, such as NIST SP 800-53, and still be compliant with the standard.
The key requirement of ISO 27001 is to ensure that all chosen controls are compared against those listed in Annex A. This comparison helps confirm that no essential controls have been overlooked and that the selected controls adequately cover the identified risks. After this comparison, organizations must produce a Statement of Applicability (SoA). The SoA is a critical document that lists all the controls from Annex A, indicates whether each control is applicable or not, and justifies why certain controls have been selected or omitted. So, it doesn't matter if you select controls from other sources than Annex A, as long as you produce a SoA that meets the requirements of ISO/IEC 27001.


