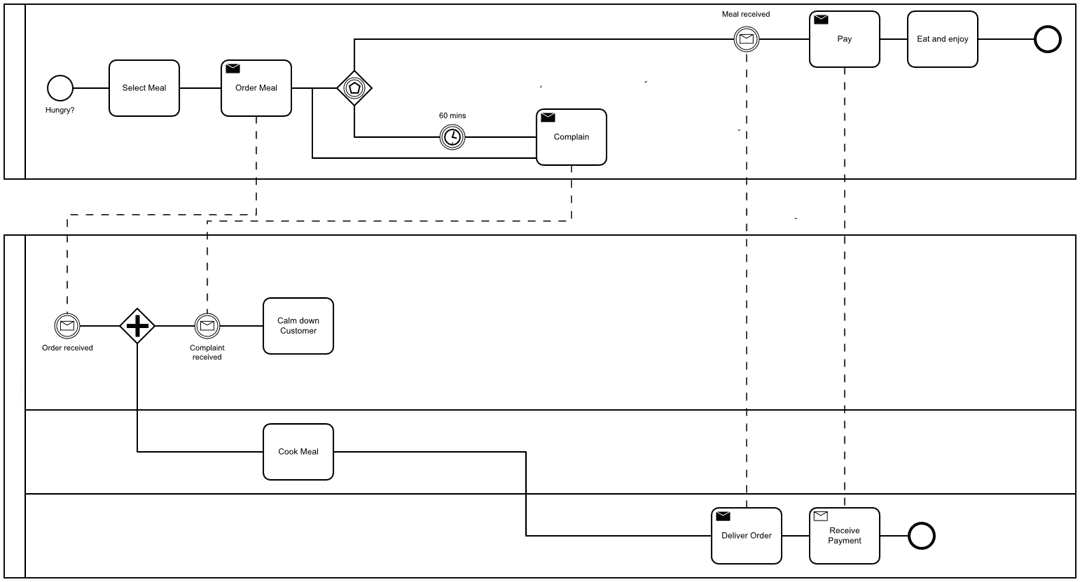
Can you explain the difference between a process and a procedure?
I have to admit, I couldn’t.
This is why, I have done some research and created this article.
In the following we are going to discover the differences between processes and procedures and how a Process Reference Model (PRM) can help to align Policies, Standards and Procedures with activities related to information security.
A solid information security documentation is foundational to an organization's security posture. It typically consists of:
Policies: High-level statements of intent and direction set by management.
Standards: Specific mandatory requirements, rules, and configurations.
Procedures: Detailed step-by-step instructions to achieve policy objectives.
Guidelines: Recommended practices that are not mandatory but advised.
While policies, standards, procedures, and guidelines are the traditional components of cybersecurity documentation, the concept of 'processes' is often absent. This is not to say that processes are unimportant; on the contrary, they are vital for understanding the broader context and flow of how various tasks and activities contribute to achieving information security objectives. However, processes are often not considered to be a part of formal documentation.
Let’s explore why that might be the case.
What is a Process?
According to ISO 9000:2015, a process is defined as:
“A set of interrelated or interacting activities that uses or transforms inputs to deliver a result.”
In other words, processes are about creating value by transforming inputs into more useful and higher-order outputs. This is achieved through a series of activities. They are interconnected and often dependent on the preceding steps. The efficiency and effectiveness of a process depend on how well these activities are planned and executed. This is why procedures are needed.

More information and guidance on processes can be found on my YouTube Channel.
What is a Procedure?
According to ISO 30000:2009, a procedure is defined as:
“A specified way to carry out an activity or a process.”
There you have it. Activities are outlined and described by detailed procedures. These documents help to ensure that each step is executed with precision and consistency, contributing to the overall objective of delivering the intended results of the overarching process.
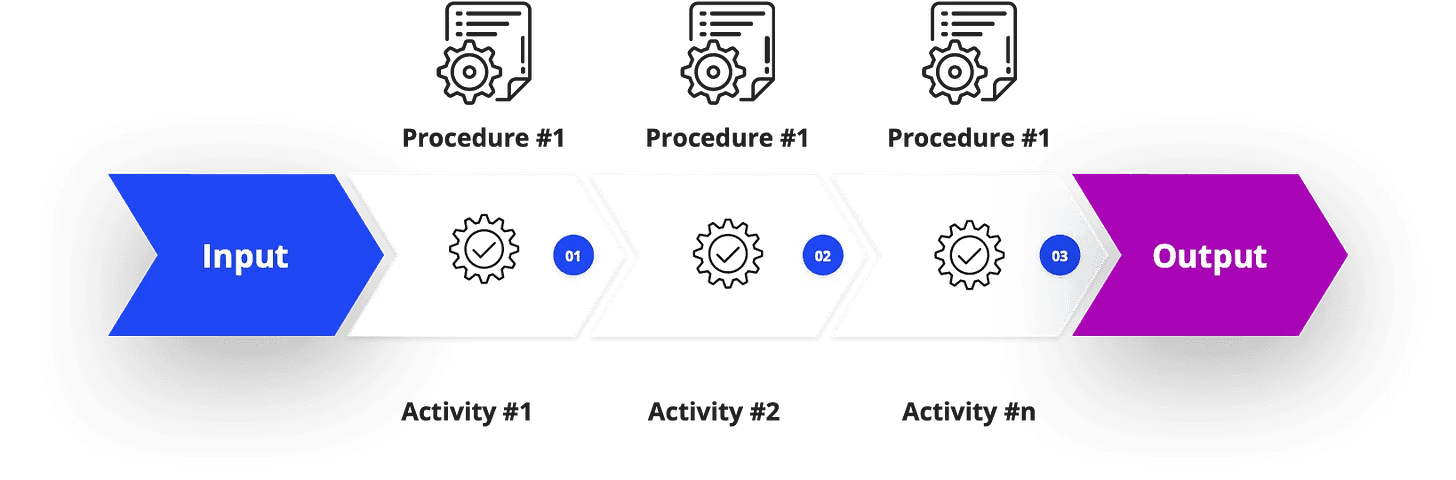
Process Reference Model
All procedures are related to processes and support them to deliver the desired results.
A Process Reference Model (PRM) is a framework that provides a structured representation of processes within an organization.
Process Reference Models (PRM) distinguish between three types of processes:
Management Processes: These processes define the objectives of the management system, including IS governance and management interface processes.
Core Processes: These are the main elements of the ISMS, delivering direct customer value. They include security policy management, information security (IS) risk assessment, IS risk treatment, outsourced services control, and IS improvement processes, among others.
Support Processes: These processes provide and manage necessary resources without delivering direct customer value. Examples include record control, resource management, communication processes, and IS customer relation processes.
Each process is detailed with the following elements:
Process category
Brief description
Objectives/purposes
Inputs
Results
Activities/functions
References (to other ISMS standards/clauses).
The activity element allows us to create a direct relationship between processes and procedures. Each activity must be described by one procedure. It is of course possible to outline several activities in one procedure to minimise the number of documents. Just make sure that an activity is not described by more than one procedure at the same time, as this might lead to confusion and contradictions.
ISO 27022 provides a PRM for information security management systems in the context of ISO 27001.
It contains the following processes, categorised into management, core and support processes:
Management Processes
Information Security Governance Interface Process
Core Processes
Security policy management process
Requirements management process
Information security risk assessment process
Information security risk treatment process
Security implementation management process
Process to control outsourced services
Process to assure necessary awareness and competence
Information security incident management process
Information security change management process
Internal audit process
Performance evaluation process
Information security improvement process
Support Processes
Records control process
Resource Management process
Communication process
Information security customer relationship management process
For each of the listed activities a corresponding procedure can be defined, which will link the process with the procedures.