Have you been in this position?
As part of your role in overseeing your organization's ISMS, you often find yourself coordinating with colleagues for evidence, generating reports, and updating documentation, even when it stretches beyond your designated duties.
Here might be the solution to your problem.
Process Reference Model
All activities within an ISMS should be embedded in a set of processes to ensure the delivery of results and continuous improvement, enabling organizations to meet their security objectives effectively and efficiently.
A Process Reference Model (PRM) is a framework that provides a structured representation of processes within an organization.
Process Reference Models (PRM) distinguish between three types of processes:
Governance Processes: These processes define the objectives of the management system, including IS governance and management interface processes.
Core Processes: These are the main elements of the ISMS, delivering direct customer value. They include security policy management, information security (IS) risk assessment, IS risk treatment, outsourced services control, and IS improvement processes, among others.
Support Processes: These processes provide and manage necessary resources without delivering direct customer value. Examples include record control, resource management, communication processes, and IS customer relation processes.
For an information security management system, the following processes are needed.
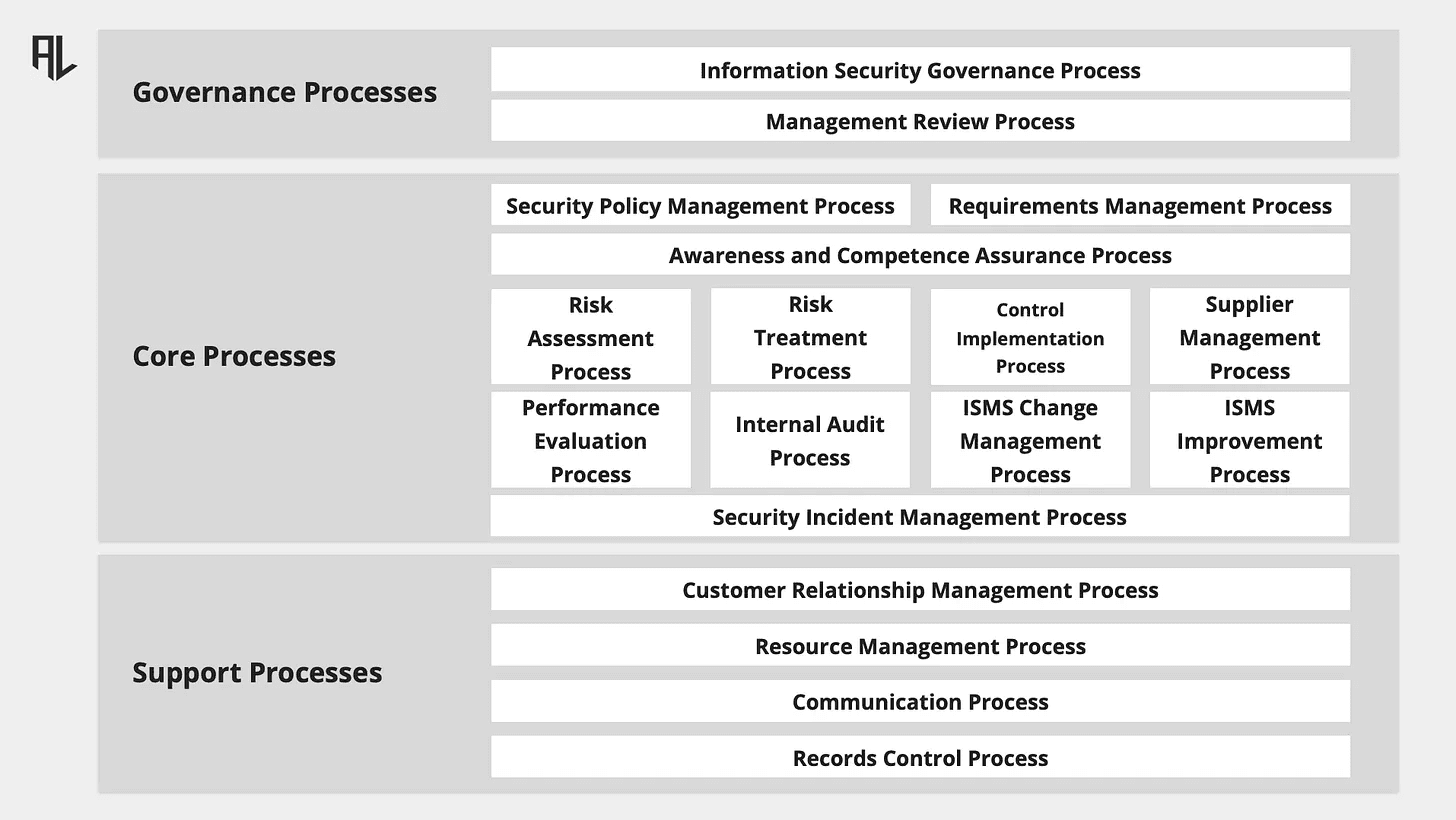
Governance Processes
Information Security Governance Process
Management Review Process
Core Processes
Security policy management process
Requirements management process
Risk assessment process
Risk treatment process
Control implementation process
Supplier management process
Competence and awareness assurance process
Information security incident management process
ISMS change management process
Internal audit process
Performance evaluation process
ISMS improvement process
Support Processes
Records control process
Resource Management process
Communication process
Customer relationship management process
Example Process
Let’s have a closer look at the information security policy management process.

Process Input
The activities within this process are provided with input from all other ISMS processes, which is necessary to create policies that put the entire organisation into consideration.
In addition, change requests to make updates to already exisiting policies are provided in the form of change requests, coming from the ISMS change management process.
Process Output
The output is a set of up to date information security policies (this includes, standards, guidelines and procedures as well).
This process encompasses the entire lifecycle of a policy, starting from its development and approval, to its distribution, secure storage, and change management, followed by its retention period and eventual disposal.
P.S.: You can find all processes in my ISO 27001 Starter Kit. Simplify your path to ISO/IEC 27001 with a customizable project plan and supporting resources.
New Video
I tried my best to explain information security / cybersecurity risk management in less than 5 minutes. You decide if I was successful.