Security incident management, business continuity management and disaster recovery planning are often considered seperate disciplines. While that may be true, they still share one common objective. The recovery of business operations during or after a threat event.
In this article we will explore the relationship between incident response, business continuity planning and disaster recovery planning.
To begin with, let’s have a closer look at security events and security incidents. Threat events seek to exploit vulnerabilities in order to harm information assets. Not all events are harmful or manage to inflict damage to an organisation. However in case the event has impacted the confidentiality, integrity or availability of one or more inforamtion assets, then the event is classified as an information security incident. This means the incident requires an immediate response to contain the adverse effects and eradicate the cause of the incident. Normale operations need to be restored as quickly as possible.
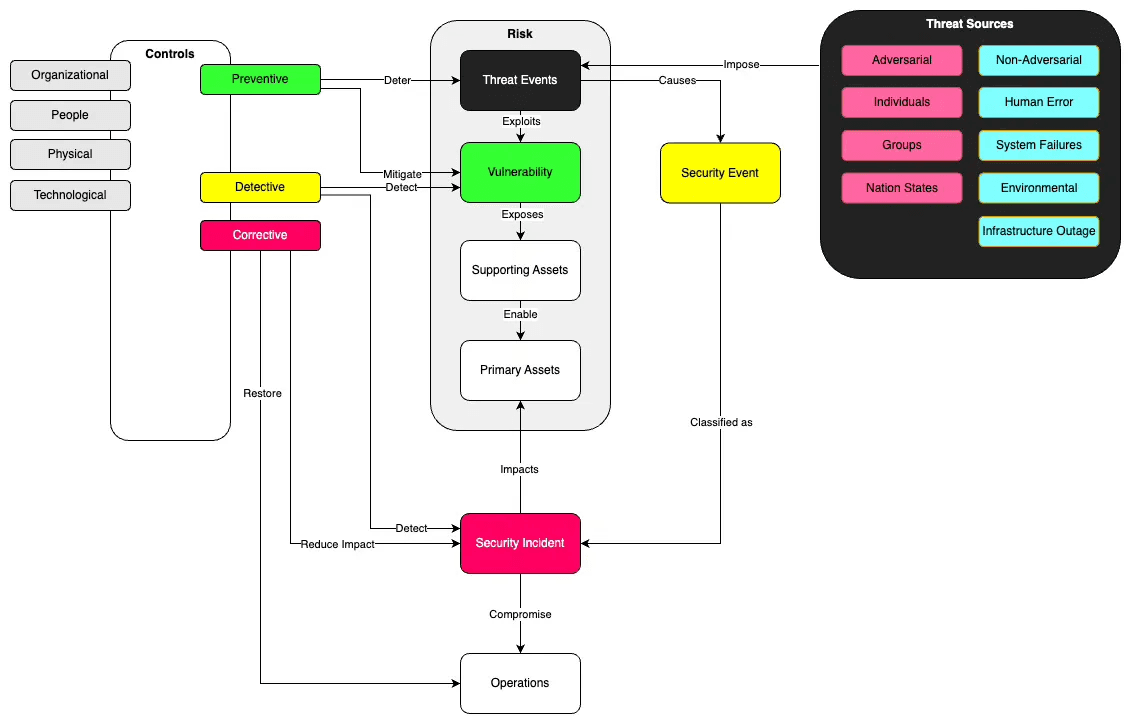
Information assets are protected by security controls. There are three ways of dealing with information security incidents. In the best case, incidents can be prevented from happening in at all. When an incident has occured, it is vital to detect them as quickly as possible. This allows for an immediate response which will correct the adverse effects and restore normale operations.
Controls can be classified according to their desired effect.
Control Types
Controls can be distinguished into the following categories.
Preventive controls
Detective controls
Corrective controls
Furthermore controls can also be categorised into the following themes.

Control Themes
In general we distinguish between organisational, people, physical and technological controls.
Technological controls are usually intangible and are implemented within in information systems. Common examples are encryption, password policies enforced by the system, etc.
Physical controls are tangible. Common examples are security gates, fences or uninterruptible power supplies.
Organisational controls are the policies, procedures and guidelines defined by an organization to provide guidance on how certain activites are supposed to be carried out.
People controls are controls that affect human beings.

Response Plan Selection
Not all incidents can be prevented from happening. Depending on the severity of the incident, the appropriate response plans need to be selected and enacted.
Information assets are impacted, but critical business functions are still running: Incident response plan
Information assets and critical business functions are impacted: Business continuity plan
Information assets are impacted and critical business functions have stopped: Disaster recovery plan

Incident Response Plan
This plan is an organized approach to addressing and managing the aftermath of a security incident. Its objective is to swiftly identify and mitigate them, minimizing impact and preventing reoccurrence. The plan outlines clear procedures for detection, analysis, containment, eradication, and recovery, ensuring a rapid and effective organizational response to safeguard critical assets.
Business Continuity Plan
If an incident has impacted critical business functions, it is no longer subject to incident response. The business continuity plan outlines procedures for sustaining critical operations during and after crises. It encompasses strategies to ensure operational resilience and continuity, encompassing risk management, resource allocation, and contingency planning. This plan is integral for preserving service delivery and stakeholder confidence, even under adverse conditions.
Disaster Recovery Plan
This plan is a comprehensive set of policies, tools, and procedures to enable the recovery or continuation of vital technology infrastructure and systems following a natural or human-induced disaster. It focuses on IT and data-centric recovery, ensuring quick restoration of hardware, applications, and data deemed essential for organizational functionality. The disaster recovery plan is crucial for mitigating the effects of significant disruptions and restoring normal business operations in a structured and timely manner.