The National Institute of Standards and Technology (NIST) Risk Management Framework (RMF) is a robust, system life cycle approach for managing security and privacy risks to organizations and their assets. It is designed to align with the constructs in the NIST Cybersecurity Framework, integrate privacy risk management processes, and incorporate supply chain risk management processes.
The RMF is composed of seven steps, each designed to prepare information system owners to conduct system-level risk management activities. The intent is to increase the effectiveness, efficiency, and cost-effectiveness of the RMF by establishing a closer connection to the organization's missions and business functions and improving communications among senior leaders, managers, and operational personnel.

The Seven Steps of the NIST RMF
Prepare: This step involves identifying and assigning individuals to specific roles associated with security and privacy risk management. It also includes establishing a risk management strategy for the organization that includes a determination of risk tolerance.
Categorize: This step involves categorizing the system and the information processed, stored, and transmitted by that system based on an impact analysis.
Select: In this step, security controls are selected and documented, including the implementation of a baseline set of controls.
Implement: This step involves implementing the security controls and describing how the controls are employed within the system and its environment of operation.
Assess: This step involves assessing the security controls in the system to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system.
Authorize: This step involves authorizing system operation based on a determination of the risk to organizational operations and assets, individuals, other organizations, and the Nation resulting from the operation of the system and the decision that this risk is acceptable.
Monitor: This step involves monitoring and assessing selected security controls in the system on an ongoing basis, documenting changes to the system or its environment of operation, conducting security impact analyses of the associated changes, and reporting the security state of the system to designated organizational officials.
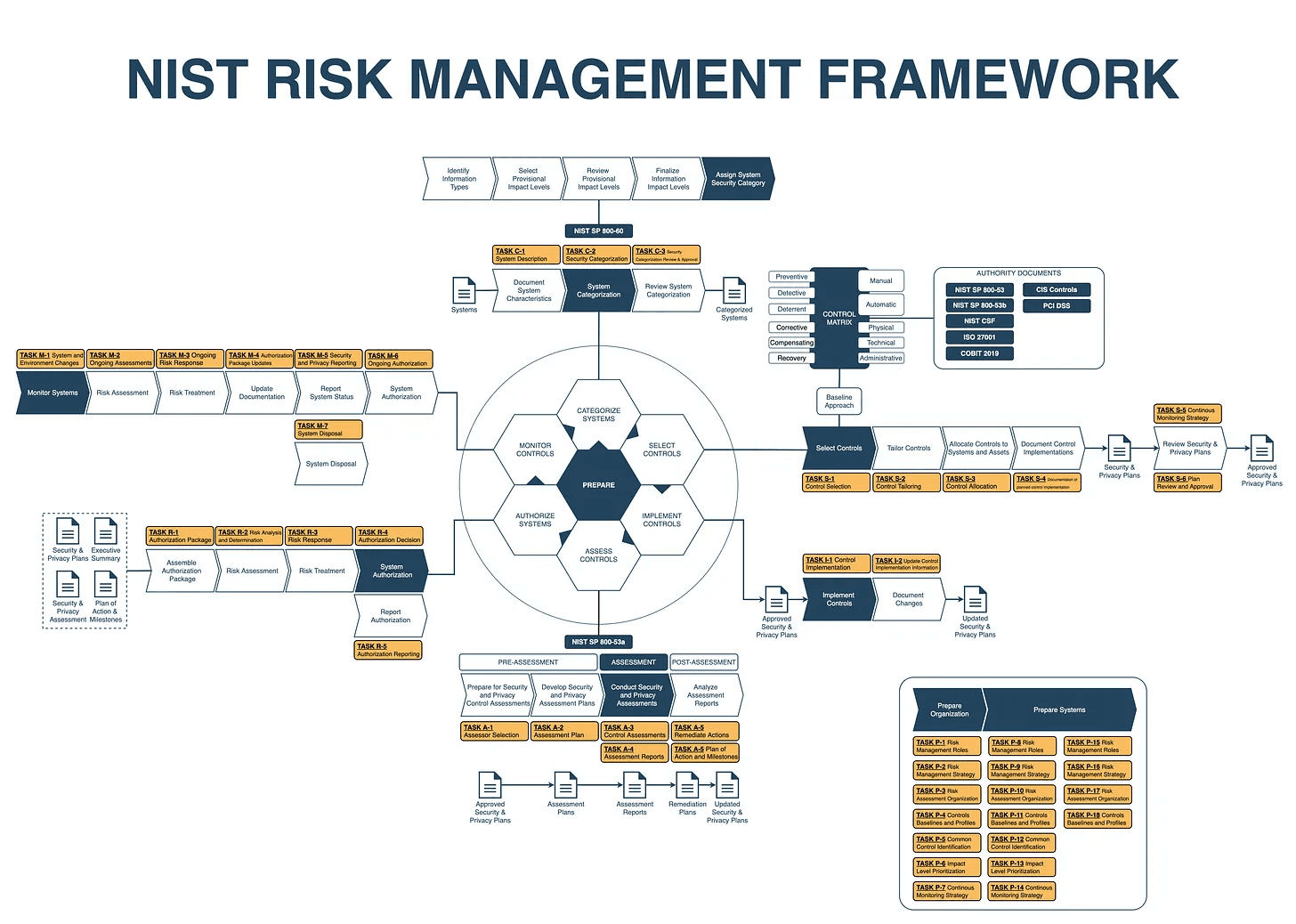
The Connection Between NIST RMF and NIST SP 800-53
The NIST Risk Management Framework (RMF) and the NIST Special Publications (SP) 800-53, 800-53A, and 800-53B are interconnected, providing a comprehensive approach to managing security and privacy risks in federal information systems.
NIST SP 800-53 and 800-53B: Selecting Controls
The third step of the RMF, "Select," requires organizations to select appropriate security controls for their information systems. This is where NIST SP 800-53 and 800-53B come into play.
NIST SP 800-53, "Security and Privacy Controls for Federal Information Systems and Organizations," provides a catalog of security and privacy controls that organizations can choose from. These controls are designed to protect the confidentiality, integrity, and availability of information systems and the data they process, store, and transmit.
NIST SP 800-53B, "Control Baselines for Information Systems and Organizations," provides guidance on selecting a baseline set of controls from the 800-53 catalog. These baselines are tailored to the specific needs of the organization and the risk it faces, taking into account factors such as the system's function, the data it handles, and the potential impact of a security breach.
NIST SP 800-53A: Assessing Controls
Once the appropriate controls have been selected and implemented, the RMF's fifth step, "Assess," comes into play. This step involves assessing the security controls to ensure they are implemented correctly, operating as intended, and producing the desired outcome.
NIST SP 800-53A, "Assessing Security and Privacy Controls in Federal Information Systems and Organizations," provides guidelines for this assessment process. It outlines a series of procedures for assessing the effectiveness of the implemented controls, helping organizations identify any weaknesses or deficiencies that need to be addressed.
In conclusion, the NIST RMF and the NIST SP 800-53, 800-53A, and 800-53B work together to provide a comprehensive, structured approach to managing security and privacy risks in federal information systems. By following these guidelines, organizations can ensure they are implementing the most effective controls for their specific needs and regularly assessing those controls to ensure they continue to provide the necessary protection.
Further Information and Resources
For those interested in delving deeper into the NIST RMF, there are several resources available that provide more detailed information:
NIST Special Publication 800-37 Revision 2: This is the official publication of the NIST RMF. It provides a comprehensive overview of the framework, including detailed descriptions of each of the seven steps and their associated tasks. The publication can be accessed for free at the following link: NIST SP 800-37 Rev. 2
NIST Risk Management Project: This project by NIST provides a wealth of information related to risk management, including the NIST RMF. The project's website includes a variety of resources, such as publications, news, and events related to risk management. You can visit the project's website at the following link: NIST Risk Management Project
These resources are excellent starting points for anyone interested in learning more about the NIST RMF and its application in managing security and privacy risks. As always, it's important to remember that the NIST RMF is a flexible framework that can be tailored to the specific needs and context of your organization.