Threat sources are entities or occurrences, whether intentional or accidental, that can potentially cause harm to an organization's information systems. Understanding these sources is crucial for risk management and for the development of effective security measures. The National Institute of Standards and Technology (NIST) provides a comprehensive guide for conducting risk assessments, including a detailed examination of threat sources, in its Special Publication 800-30.
Identifying Threat Sources
The first step in risk management is identifying and characterizing the sources of concern. This includes assessing the capabilities, intentions, and targeting aspects associated with adversarial threat sources, as well as the potential range of effects from non-adversarial threat sources.
Organizations need to consider both internal and external sources of threat information. Internal sources can include previous risk/threat assessments, while external sources can range from open-source or classified threat reports to information from peers, partners, and trusted research organizations. The timeliness, specificity, and relevance of threat information should be considered when using external sources.
Adversarial Threat Sources
Adversarial threat sources are entities that intentionally seek to exploit vulnerabilities in an organization's information systems. These sources can range from individuals with no affiliation to the organization to nation-state actors with significant resources at their disposal.
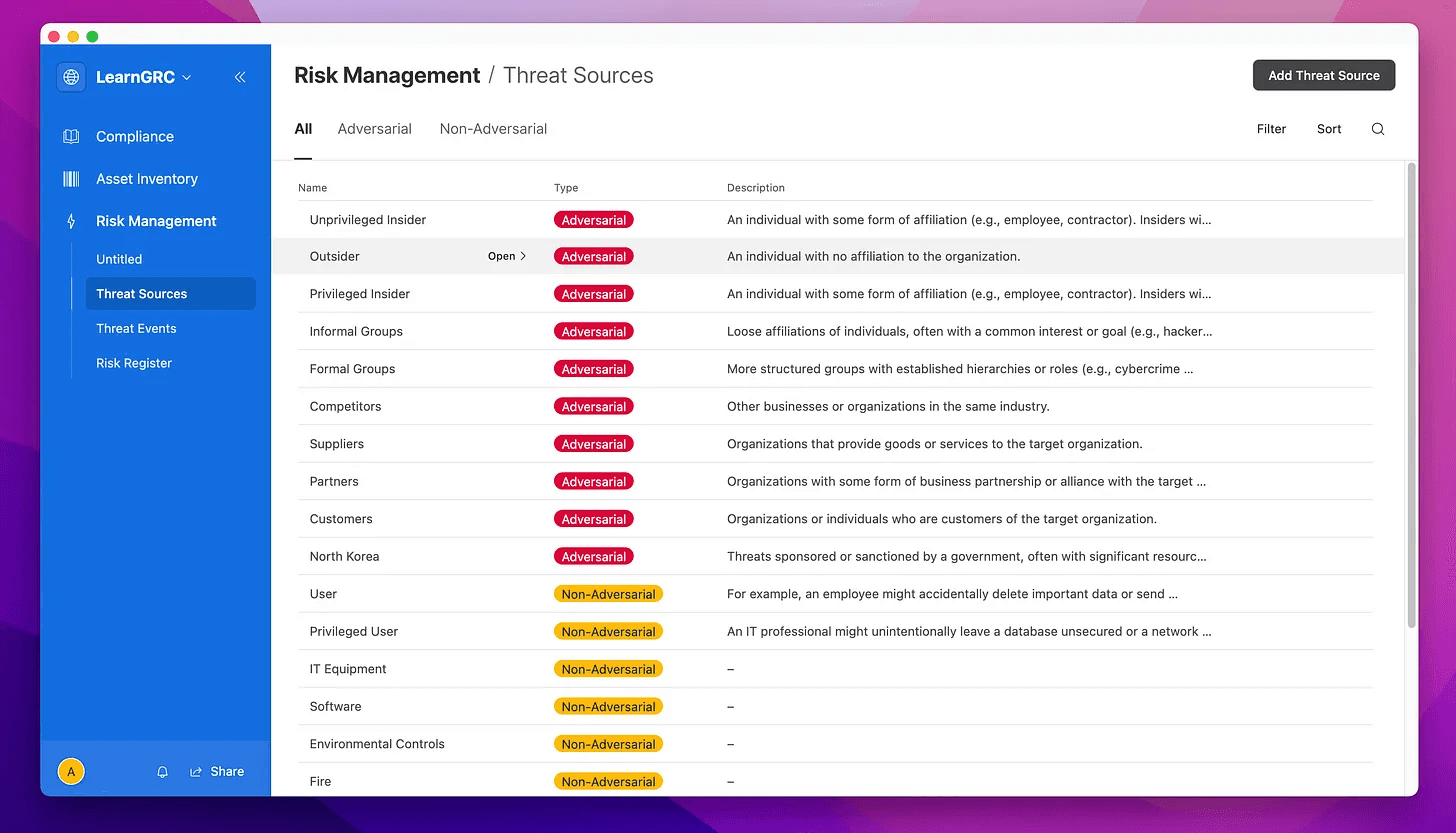
Outsider: An individual with no affiliation to the organization. They may seek to exploit vulnerabilities for various reasons, such as financial gain or ideological motives.
Privileged Insider: An individual with some form of affiliation (e.g., employee, contractor) and higher access privileges, such as administrators or executives. They may misuse their access to cause harm to the organization.
Unprivileged Insider: An individual with some form of affiliation (e.g., employee, contractor) and standard access privileges. They may unintentionally cause harm due to negligence or lack of awareness, or intentionally due to disgruntlement or coercion.
Informal Groups: Loose affiliations of individuals, often with a common interest or goal (e.g., hacker collectives). They may collaborate to exploit vulnerabilities for shared objectives.
Formal Groups: More structured groups with established hierarchies or roles (e.g., cybercrime organizations). They often have more resources and capabilities to carry out coordinated attacks.
Competitors: Other businesses or organizations in the same industry. They may seek to exploit vulnerabilities to gain a competitive advantage.
Suppliers, Partners, Customers: These entities have a business relationship with the organization and may have access to certain information or systems. They could pose a threat if they intentionally misuse this access.
Nation-State Actors: Threats sponsored or sanctioned by a government, often with significant resources at their disposal. They may target organizations for strategic, economic, or political reasons.
Characterizing Adversarial Threat Sources
Adversarial threat sources are characterized by three main factors: capability, intent, and targeting.
Capability: This refers to the technical and operational abilities of the threat source to exploit a vulnerability. For example, a nation-state actor may have advanced technical capabilities and resources that allow them to launch sophisticated cyber attacks.
Intent: This refers to the threat source's motivation or desire to exploit a vulnerability. For example, a competitor may have a strong intent to gain an advantage by stealing sensitive information.
Targeting: This refers to the direction or focus of the threat source's intent. For example, an insider may target specific information that they have access to within the organization.
Non-Adversarial Threat Sources
Non-adversarial threat sources are not intentionally malicious but can still cause harm to an organization's information systems. These sources often relate to natural events, human error, or system failures.
Examples of Non-Adversarial Threat Sources
Environmental Threats: These include natural disasters such as floods, earthquakes, or fires that can cause physical damage to an organization's infrastructure.
Human Error: This includes mistakes made by employees or contractors, such as accidentally deleting important data or falling for phishing scams.
Infrastructure Outage: This includes events like power outages or network downtime that disrupt the normal functioning of an organization's systems.
System or Equipment Failures: This includes any malfunction or failure in an organization's hardware or software. For example, a server could fail, causing a loss of data, or a software bug could cause a system to behave unpredictably.
Characterizing Non-Adversarial Threat Sources
Non-adversarial threat sources are characterized by the range of effects they can cause. This can vary widely, from minor inconveniences to major disruptions, depending on the specific characteristics of the threat source.
Conclusion
Understanding threat sources is a crucial part of risk management. By identifying and characterizing these sources, organizations can better prepare for and mitigate potential threats. The NIST Special Publication 800-30 provides a comprehensive guide for this process, offering valuable insights and tools for organizations to use in their own risk assessments.