The ISO 27000 family of standards is a set of guidelines developed by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) under the joint ISO and IEC subcommittee, ISO/IEC JTC 1/SC 27. Its purpose? To offer organizations a robust and comprehensive framework for managing and improving their information security.
The ISO 27000 series is not just one standard but a suite of inter-related standards, each providing guidelines and requirements addressing various aspects of information security. Together, they form a cohesive model for implementing and managing a robust Information Security Management System (ISMS).
The ISO 27000 family is divided into four main categories:
Standards describing overview and terminology
Standards specifying requirements
Standards describing general guidelines
Standards describing sector-specific guidelines
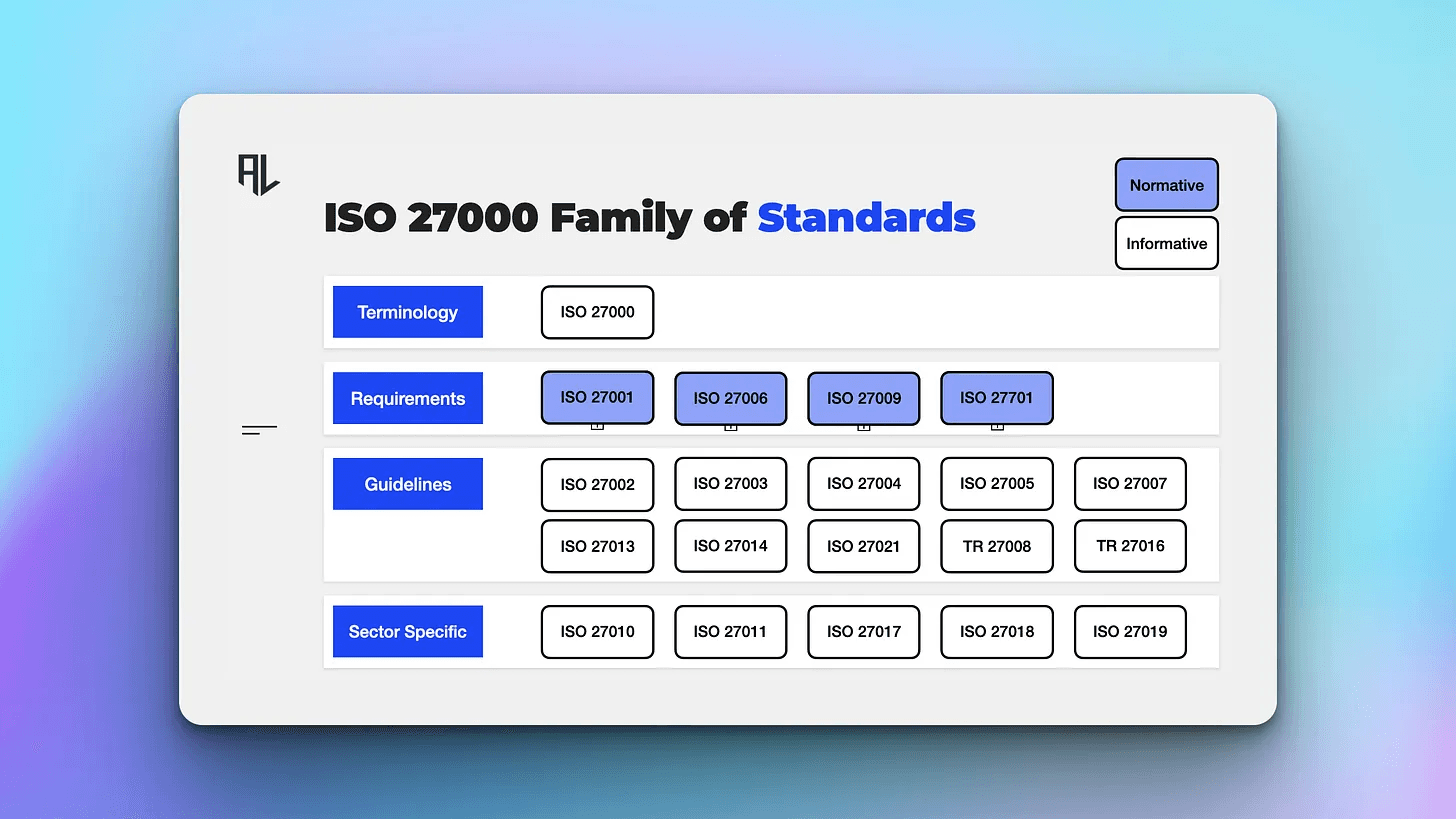
Standards Describing Overview and Terminology
These standards introduce the basic concepts and terms related to ISMS. ISO 27000 is a prime example of this category. It provides an introduction to the family of standards and defines essential terminologies, thereby setting the foundation for understanding the subsequent standards.
Standards Specifying Requirements
These are the normative standards, the ones that can be audited against. They stipulate specific requirements that an organization must fulfill to achieve compliance. The most well-known among these is the ISO 27001. This standard outlines the requirements for establishing, implementing, maintaining, and continually improving an ISMS. Achieving ISO 27001 certification is a clear demonstration of an organization's commitment to maintaining high levels of data protection and information security.
Standards Describing General Guidelines
These standards provide general guidance on the application of the normative standards, explaining how the requirements can be met. They are not intended for certification, but they offer valuable insights that organizations can use to ensure that their information security measures are robust and comprehensive. For example, ISO 27002 provides a detailed code of practice for information security controls, acting as a reference point for organizations implementing an ISMS.
Standards Describing Sector-Specific Guidelines
These standards provide additional, industry-specific guidance for certain sectors where there might be unique information security challenges or requirements. For instance, ISO 27011 offers guidelines specifically for telecommunication organizations.
I’ll explain the general structure of the ISO 27000 family of standards in the following video.
A Closer Look at Key Standards
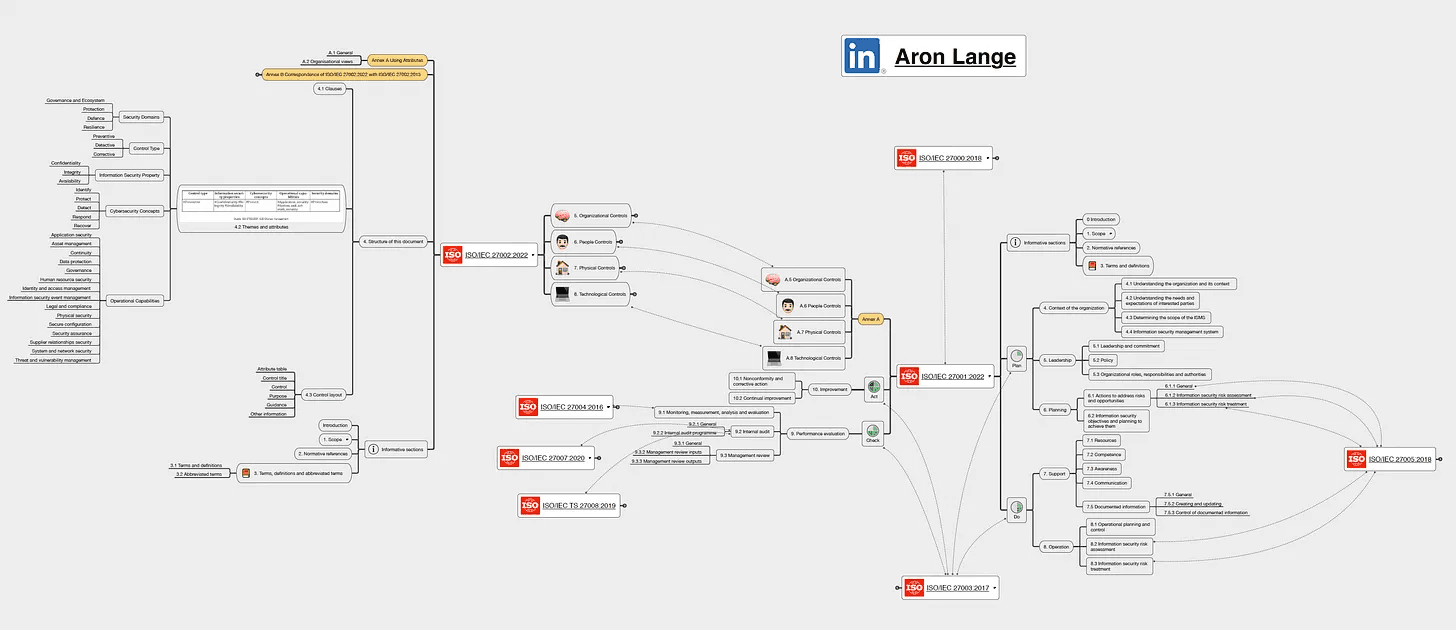
ISO 27000: Information Security Management Systems - Overview and Vocabulary
ISO 27000 provides an overview of information security management systems (ISMS) and defines related terms and definitions. This standard serves as an essential starting point and a valuable reference that helps organizations and interested parties understand the fundamental principles and vocabulary in the ISO 27000 series.
ISO 27001: Information Security Management Systems - Requirements
ISO 27001 is the cornerstone of the ISO 27000 family, specifying the requirements for establishing, implementing, maintaining, and continually improving an ISMS. Organizations can seek certification to this standard to demonstrate their commitment to information security management.
ISO 27002: Code of Practice for Information Security Controls
This standard provides a detailed set of best practices for implementing information security controls under the umbrella of the ISMS introduced in ISO 27001. It's designed to be used in conjunction with ISO 27001, providing detailed guidance on the controls that may be applied to achieve the outcomes specified by the ISO 27001 standard.
ISO 27003: Information Security Management System Implementation Guidance
ISO 27003 offers specific guidance for the implementation of an ISMS based on the requirements specified in ISO 27001. It provides a structured method for organizations to plan and implement an ISMS.
ISO 27004: Information Security Management - Monitoring, Measurement, Analysis and Evaluation
ISO 27004 provides guidance on how to assess the performance of an ISMS. It explains how to develop and implement measurement techniques and how to interpret and report on the data produced.
ISO 27005: Information Security Risk Management
This standard offers guidelines for managing information security risks. It supports the general concepts specified in ISO 27001 and is designed to assist the satisfactory implementation of information security based on a risk management approach.
ISO 27006: Requirements for Bodies Providing Audit and Certification of Information Security Management Systems
ISO 27006 provides guidelines for the accreditation of organizations offering ISMS certification, ensuring they operate in a consistent, reliable, and efficient manner.
ISO 27007: Guidelines for Information Security Management Systems Auditing
ISO 27007 provides guidance on managing an information security management system audit program, on conducting audits, and on the competence of ISMS auditors, in addition to the guidance contained in ISO 19011.
ISO 27008: Guidance for Auditors on ISMS Controls
This standard gives guidelines for the auditors on how to audit the information security controls of an organization. It provides a basis for evaluating the implementation and effectiveness of the controls identified in ISO 27002.
Learn more about how the different standards connect and relate with each other in the following video.
It's important to note that while only normative standards can be audited for compliance, all the standards in the ISO 27000 family play vital roles in establishing and maintaining an effective ISMS. The informative standards, though not auditable, provide essential guidance that can help organizations understand and effectively implement the requirements of the normative standards.
In conclusion, the ISO 27000 family of standards offers a well-structured and comprehensive blueprint for organizations striving to manage and enhance their information security. By understanding and implementing these standards, organizations not only secure their information assets but also demonstrate their commitment to information security to stakeholders, customers, and regulatory bodies. Adopting the ISO 27000 standards can be a strategic step towards building trust, fostering growth, and ensuring resilience in the face of ever-evolving information security threats.