In the last article we have explored the basic components of an ISMS and how they interrelate with each other with special regards to risk management.
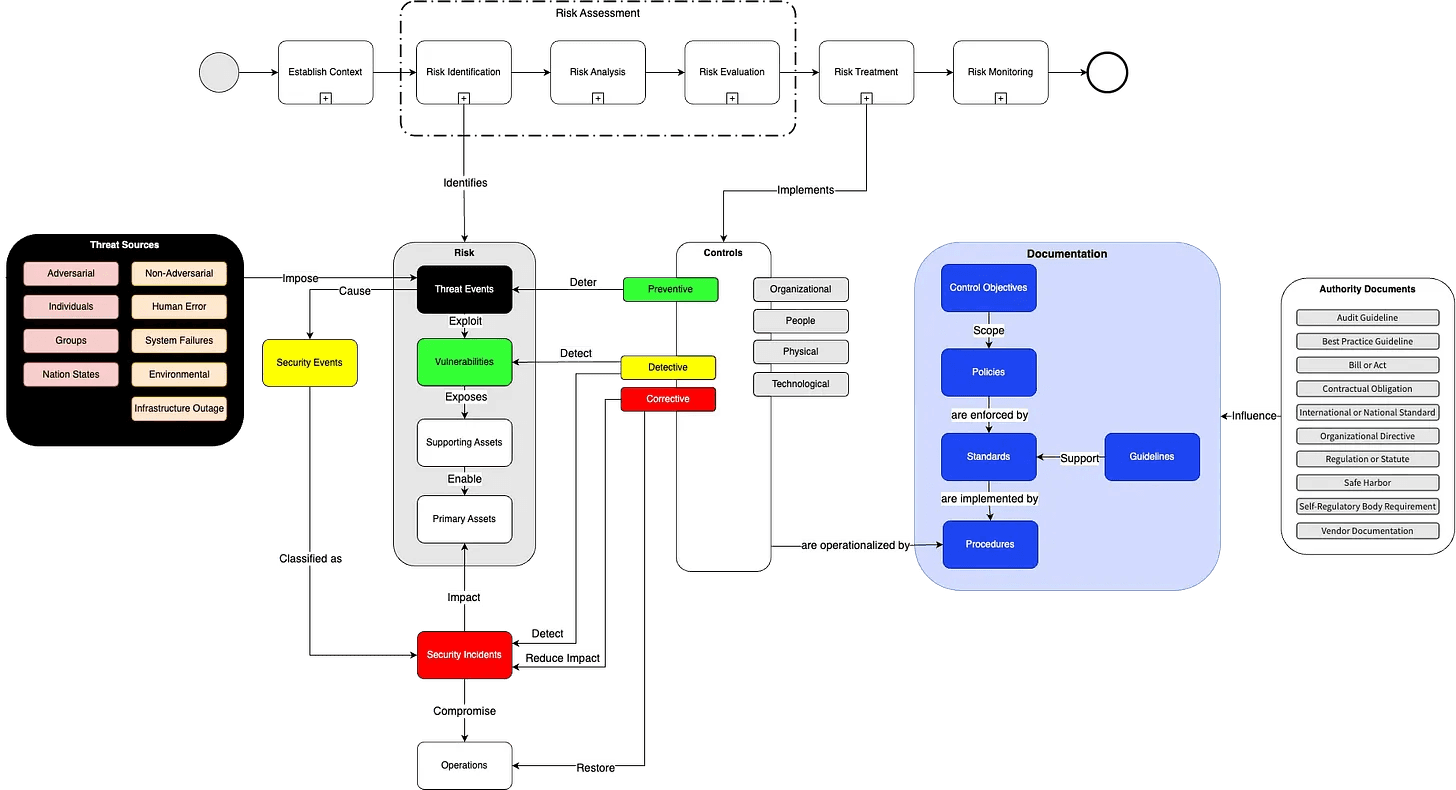
Documentation is the backbone of an effective Information Security Management System (ISMS). Clear, concise, and well-structured documentation is critical for aligning and harmonising the actions in terms of information security within an organization. This article delves into the structure and types of documents essential for a robust ISMS.
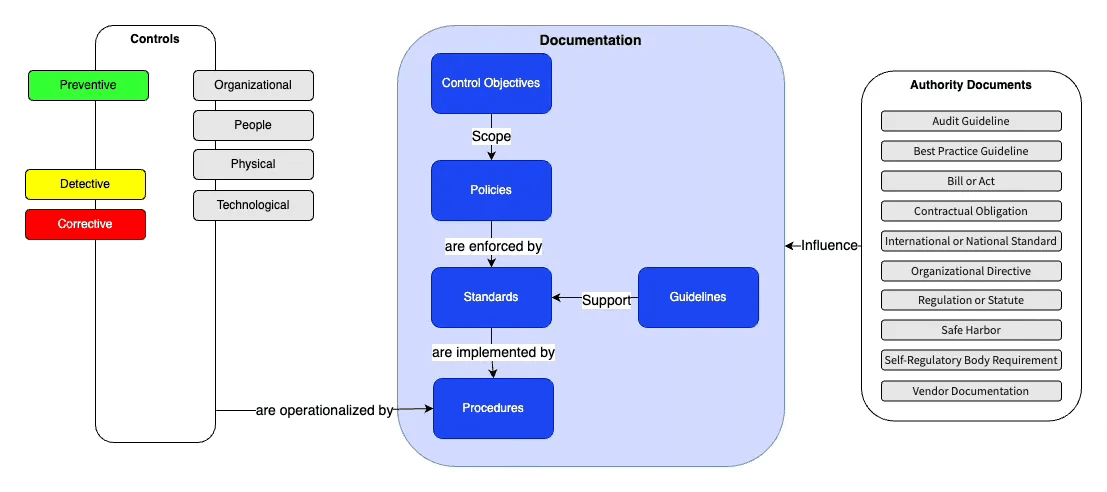
An effective documentation typically consists of the following types of documents:
Policies
Standards
Procedures
Guidelines
Overview of Document Types
Policies
Purpose: Policies outline the intent, vision and direction for information security of top management. Policies are enforced by standards and are brought into life by procedures.
Structure:
Introduction: Define the scope and purpose of the policy.
Policy Statement: State management's intent in clear, unambiguous language.
Roles and Responsibilities: Identify the roles within the organization that will be responsible for policy enforcement.
Review and Update: Specify the frequency and method of policy review.
Example: An "Access Control Policy" might outline the company's commitment to managing and restricting who can access certain information, detailing how permissions are granted, monitored, and revoked.
Control Objectives
Purpose: Control objectives are explicit statements that describe what is to be achieved as a result of implementing particular controls. They are set to achieve specific outcomes in the information security program.
Control objectives can be influenced by authority documents that organisations need to or want to comply with.
Standards
Purpose: Standards provide detailed, measurable characteristics that need to be satisfied or achieved for compliance. They are usually technical and outline the “how-to” part of meeting control objectives.
Structure:
Scope: Clearly define what the standard applies to.
Requirements: Measurable specifications that need to be satisfied.
Compliance: Statement on the verification method and penalties for non-compliance.
Example: A "Password Standard" could specify that all passwords must be at least 12 characters long, include a mix of numbers, symbols, and both upper and lower-case letters.
Procedures
Purpose: Procedures are step-by-step instructions on how to perform specific tasks, aimed at achieving a control objective or compliance with a standard.
Example: A "Data Backup Procedure" might detail the steps for taking daily backups, specifying the software to use, the data to back up, and the storage location.
Guidelines
Purpose: Guidelines offer non-mandatory advice and best practices on how to execute certain tasks. They are recommendations that provide a degree of flexibility.
Structure:
Overview: General description of what the guideline covers.
Suggestions: Detailed advice or best practices.
Exceptions: Cases where the guidelines may not apply.
Example: A "Remote Work Guideline" might suggest best practices for securing home Wi-Fi but leave it up to individual employees whether to implement them.

Another look at the different components of a documentation structure.
Documented Information and ISO 27001
A short lecture on how to fulfil the requirements towards documented information in the context of ISO/IEC 27001, the international standard on information security management systems.